Getting Started Overview
🚀 Welcome to AlertD Setup
This guide will walk you through deploying AlertD in your AWS environment and connecting your infrastructure. The entire process takes about 25-35 minutes and consists of two main phases.
📋 What You’ll Need Before Starting
Before beginning the deployment, make sure you have:
AWS Requirements
-
AWS Account with appropriate permissions
- CloudFormation stack creation and management
- IAM role creation and policy attachment
- ECS, VPC, ALB, Secrets Manager, and CloudWatch access
- Ability to create service-linked roles for ECS/ELB
-
Supported AWS Region
- AlertD supports the following regions:
Region Group Region Codes US us-east-1, us-east-2, us-west-1, us-west-2 Europe eu-central-1, eu-north-1, eu-south-1, eu-south-2, eu-west-1, eu-west-3, il-central-1, me-central-1 Asia-Pacific ap-northeast-1, ap-northeast-2, ap-northeast-3, ap-south-1, ap-south-2, ap-southeast-1, ap-southeast-2, ap-southeast-3, ap-southeast-4, ap-southeast-5, ap-southeast-7 -
DNS Domain & SSL Certificate
- A domain name you control (e.g.,
alertd.example.com) - An ACM SSL/TLS certificate in the same region where you’ll deploy
- Request a public certificate in ACM or import an existing certificate
- A domain name you control (e.g.,
-
LLM Provider Choice
- Amazon Bedrock (Claude) - Fully managed through AWS, no external API calls
- OpenAI - Requires OpenAI API key
- Anthropic - Requires Anthropic API key (direct, not via Bedrock)
Authentication Provider
- Google Account or GitHub Account for team authentication
- You’ll use this to set up your AlertD workspace and authorize team members
Network Access
Your deployment and end-user browsers must be able to reach:
- auth.demo.alertd.ai over TCP 443
- api.openai.com over TCP 443 (if using OpenAI as LLM provider)
🗺️ Setup Roadmap
Phase 1: Deploy AlertD Infrastructure
In this phase, you’ll:
- Subscribe to AlertD on AWS Marketplace (free during design partner phase)
- Deploy the AlertD CloudFormation stack to your AWS account
- Configure networking (new or existing VPC)
- Set up load balancer and ECS Fargate services
- Configure your chosen LLM provider
Time: ~15-20 minutes
Phase 2: Initial Setup & Authentication
Once deployed, you’ll:
- Access the AlertD application URL from CloudFormation outputs
- Connect your Google or GitHub account for authentication
- Create an IAM role with read-only access to your AWS resources
- Configure the AlertD agent to access CloudWatch
Time: ~10-15 minutes
🏗️ Architecture Overview
AlertD deploys as a fully containerized web application on AWS ECS Fargate. You have two deployment options:
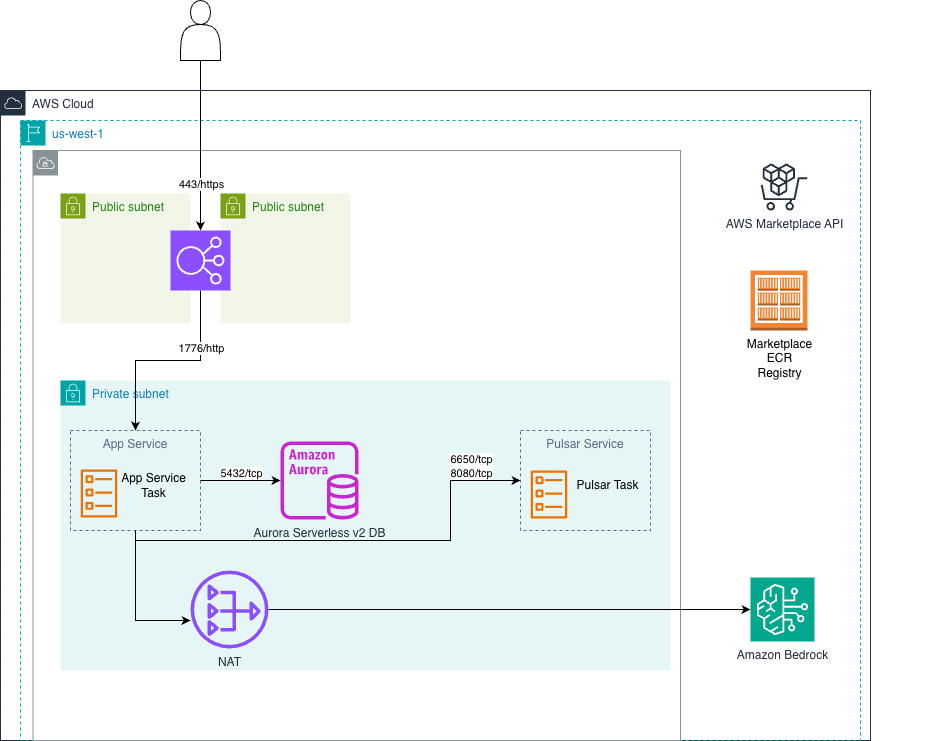
Public Load Balancer Deployment
Standard deployment with a public Application Load Balancer for end-user access via HTTPS.
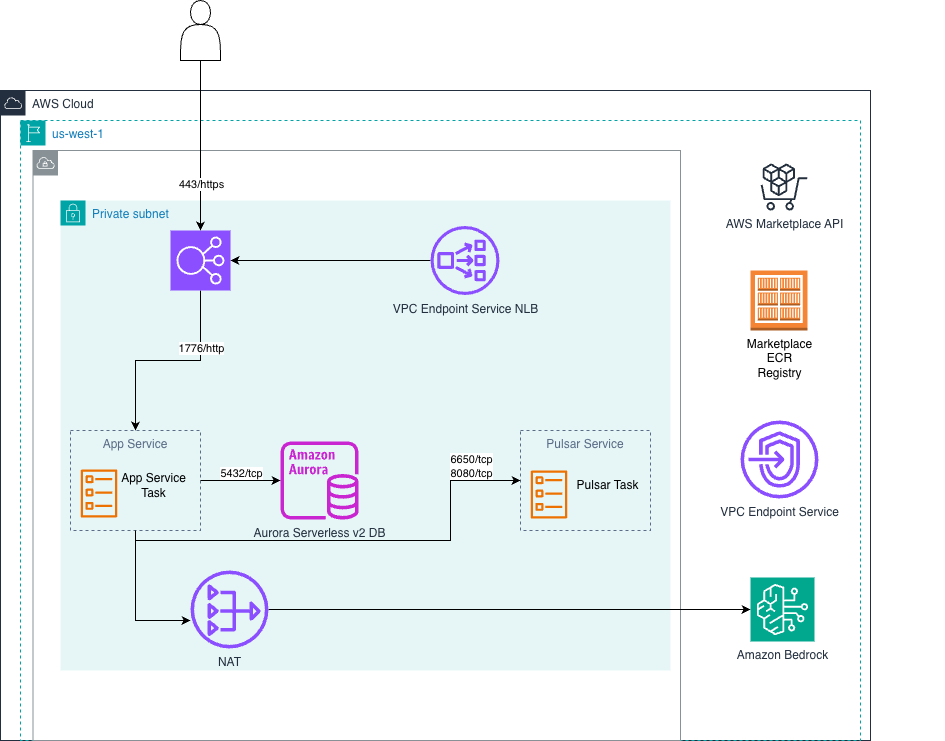
Private Load Balancer Deployment
Fully private deployment using a private ALB, suitable for organizations requiring all traffic to remain within their VPC.
🔒 Security Model
AlertD is designed with security as a top priority:
- Read-Only Access: AlertD only requests CloudWatch read permissions
- Ephemeral Credentials: Uses AWS STS tokens, not permanent access keys
- No Write Permissions: Cannot modify, change, or write to any AWS infrastructure
- Immediately Revocable: Remove the IAM role at any time to revoke access
- Encrypted Transit: All data transmission uses 256-bit encryption
🆘 Design Partner Support
During the design partner phase, AlertD support may need temporary access to gather usage metrics. If deploying with a private load balancer, you can provide access via VPC endpoint service. This access will be disabled before production usage.
✅ Ready to Begin?
Once you have all prerequisites ready, proceed to the deployment guide.