Deploying AlertD to AWS
This guide walks you through deploying AlertD to your AWS account using CloudFormation. The deployment creates a fully managed, containerized application running on ECS Fargate with all supporting infrastructure.
Estimated time: 15-20 minutes
Step 0: Subscribe to AlertD on AWS Marketplace
AlertD is available on the AWS Marketplace and is free of charge during the design partner phase.
Prerequisites for Subscription
Design partners must first share their AWS account ID with the AlertD team so we can whitelist it. Once whitelisted, you can proceed with the subscription.
Subscribe to AlertD
- Visit the AWS Marketplace listing: AWS Marketplace - AlertD
- Click Continue to Subscribe
- Accept the terms and complete the subscription process
- This subscription ensures smooth integration with your AWS environment and enables support during the design phase
Once subscribed, proceed with the CloudFormation deployment below.
Step 1: Open CloudFormation Console
- Sign in to your AWS Management Console
- Navigate to CloudFormation → Stacks
- Ensure you’re in the correct AWS region where you want to deploy AlertD
- Verify the Stacks view is displayed
Step 2: Create a New Stack
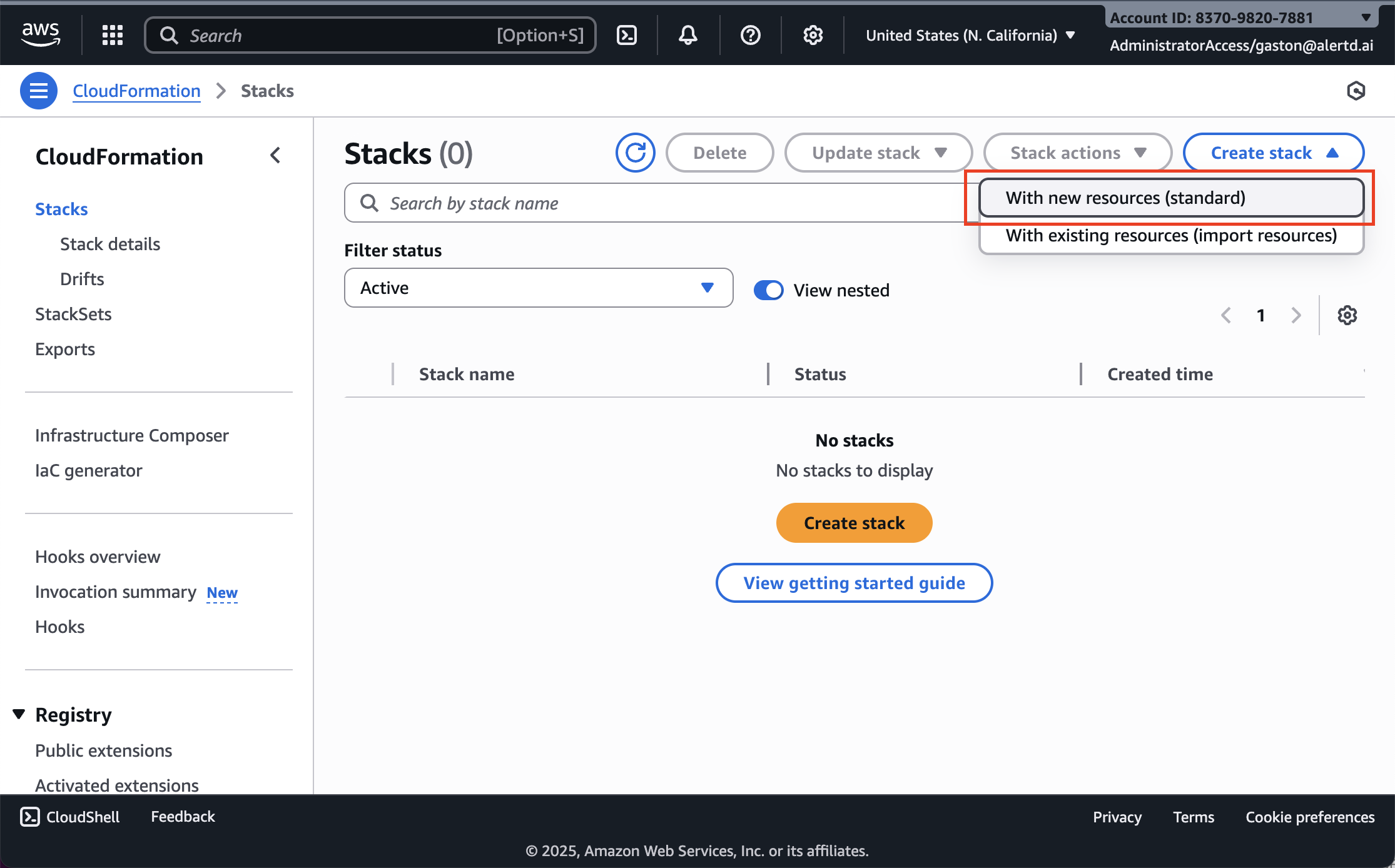
- Click Create stack
- In the dropdown, select With new resources (standard)
- This will initiate a new CloudFormation stack deployment
Step 3: Specify the AlertD Template
- Under Prerequisite – Prepare template, select Choose an existing template
- Under Specify template, select Amazon S3 URL
- Paste the following AlertD CloudFormation template URL:
https://alertd-publicassets.s3.us-west-1.amazonaws.com/cloudformation/AlertD_RDS.yaml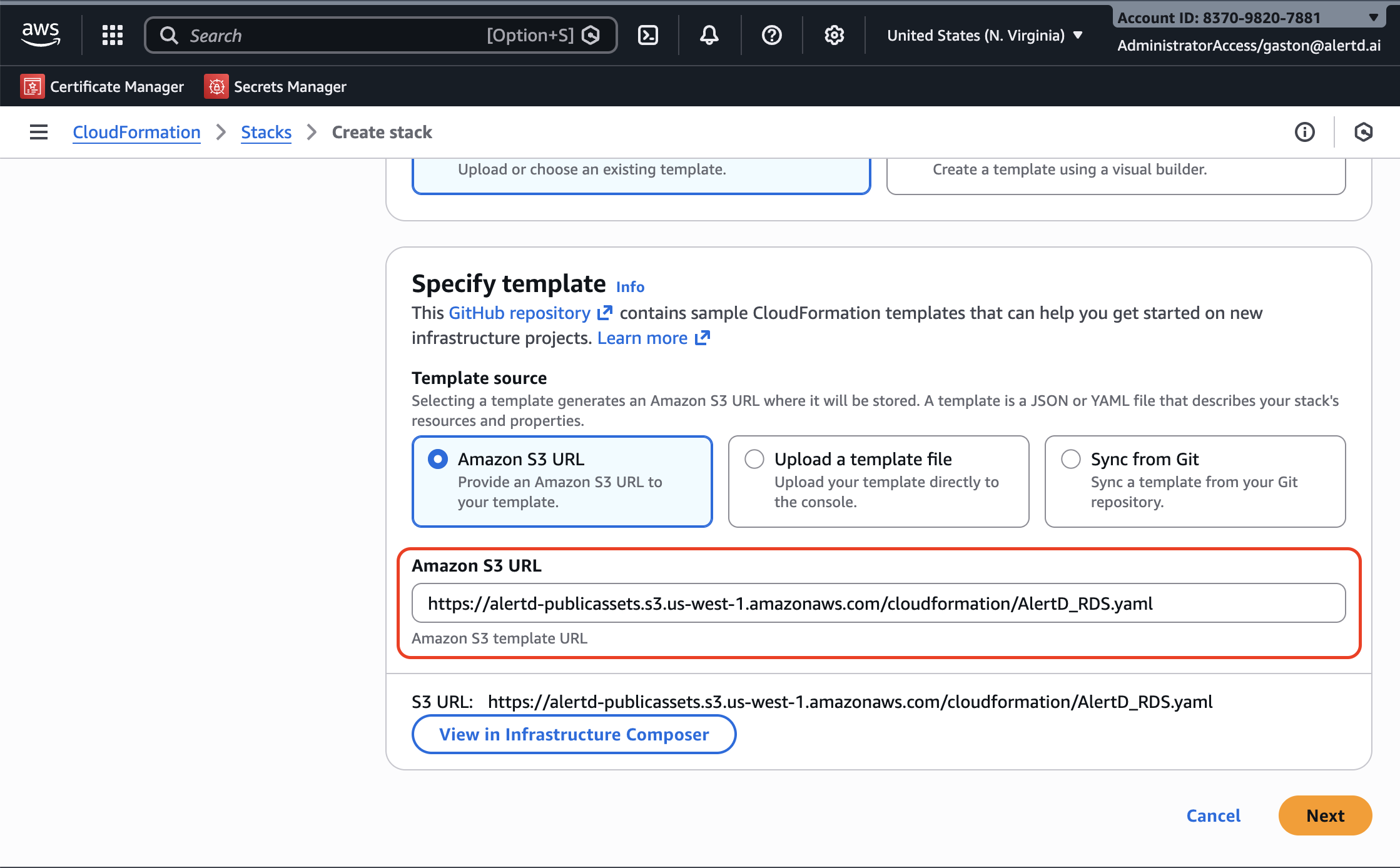
- Click Next to proceed to stack configuration
Step 4: Configure Stack Name and Certificate
Stack Name
Enter a descriptive stack name:
AlertD-Stack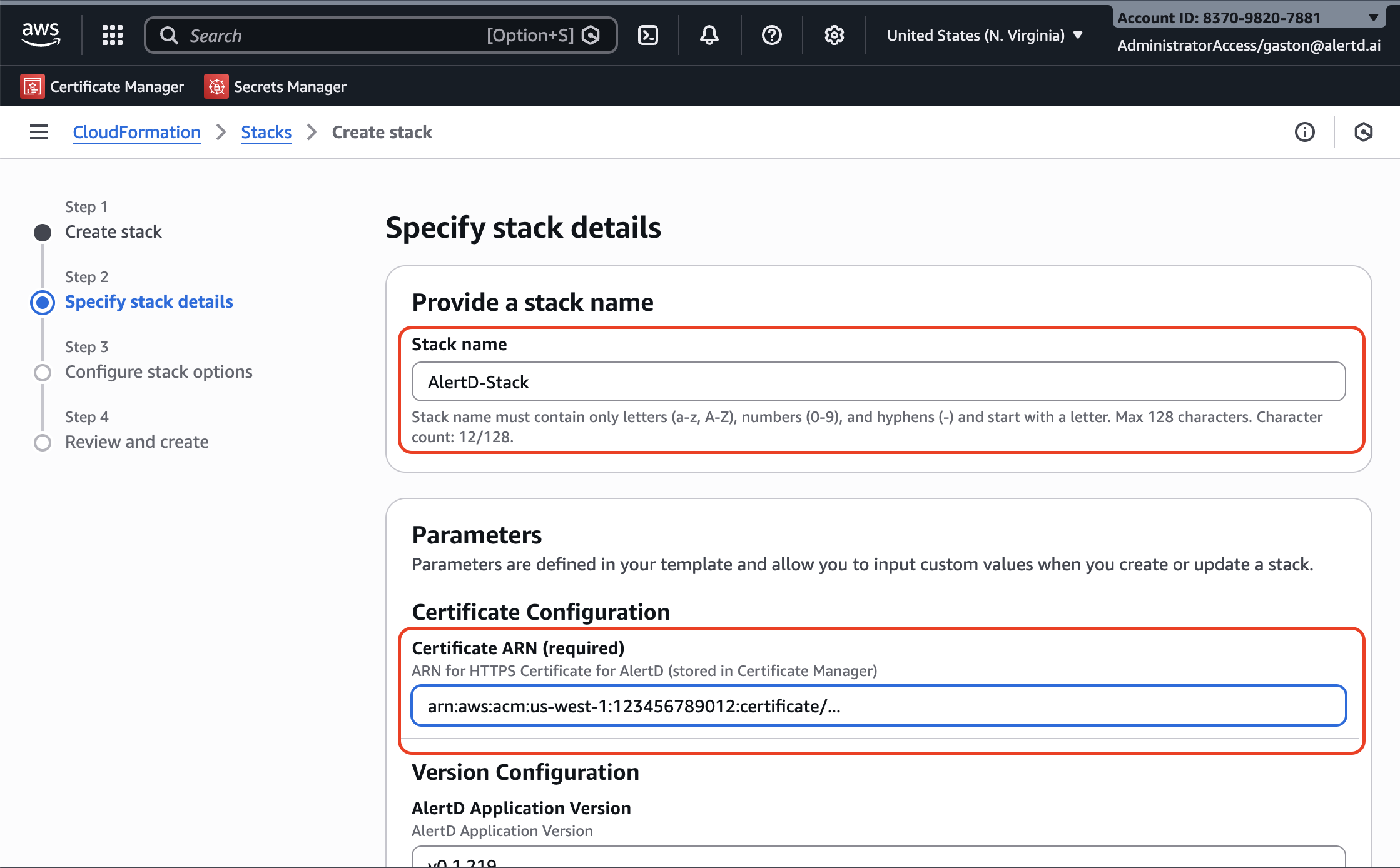
Certificate Configuration (Required)
Certificate ARN: Paste the ARN of your validated SSL certificate from AWS Certificate Manager (ACM).
- The certificate must be in the same region where you’re deploying AlertD
- Format:
arn:aws:acm:us-west-1:123456789012:certificate/... - If you don’t have a certificate yet, see the prerequisites guide
Step 5: Configure LLM Model Provider
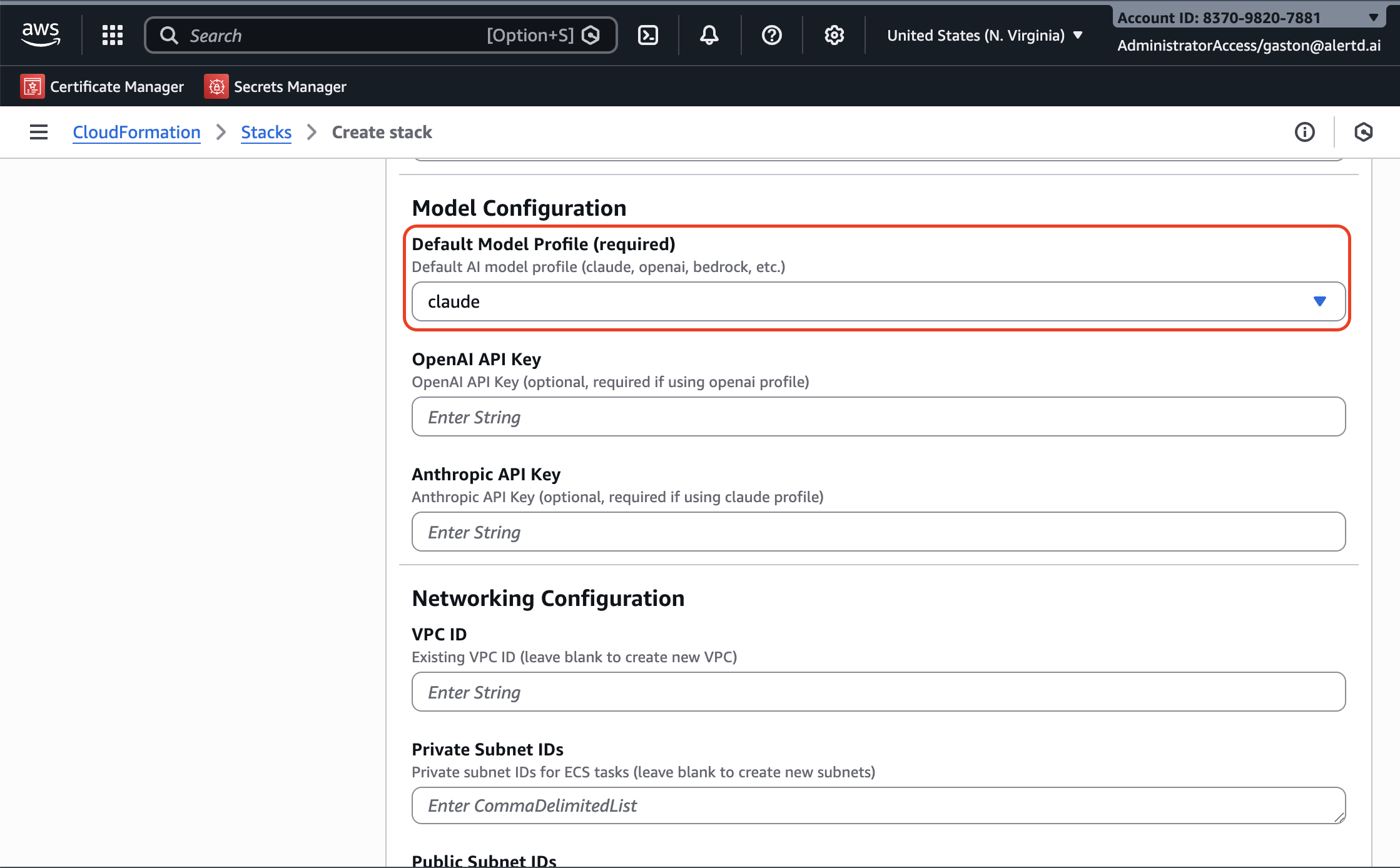
Default Model Profile (Required)
Choose your preferred AI model provider:
-
claude– Uses Anthropic Claude via Amazon Bedrock- Fully managed through AWS
- No external API calls
- Recommended if your organization already uses Bedrock
-
openai– Connects to OpenAI’s API (e.g., GPT models)- Requires entering your OpenAI API key below
-
anthropic– Uses Anthropic Claude directly through Anthropic’s public API- Not via Bedrock
- Requires your Anthropic API key below
API Keys (If Applicable)
- OpenAI API Key: Enter your key if you selected
openaiprofile - Anthropic API Key: Enter your key if you selected
anthropicprofile
API keys will be stored securely in AWS Secrets Manager. Ensure you’re using the correct key for your chosen provider.
Step 6: Configure Networking
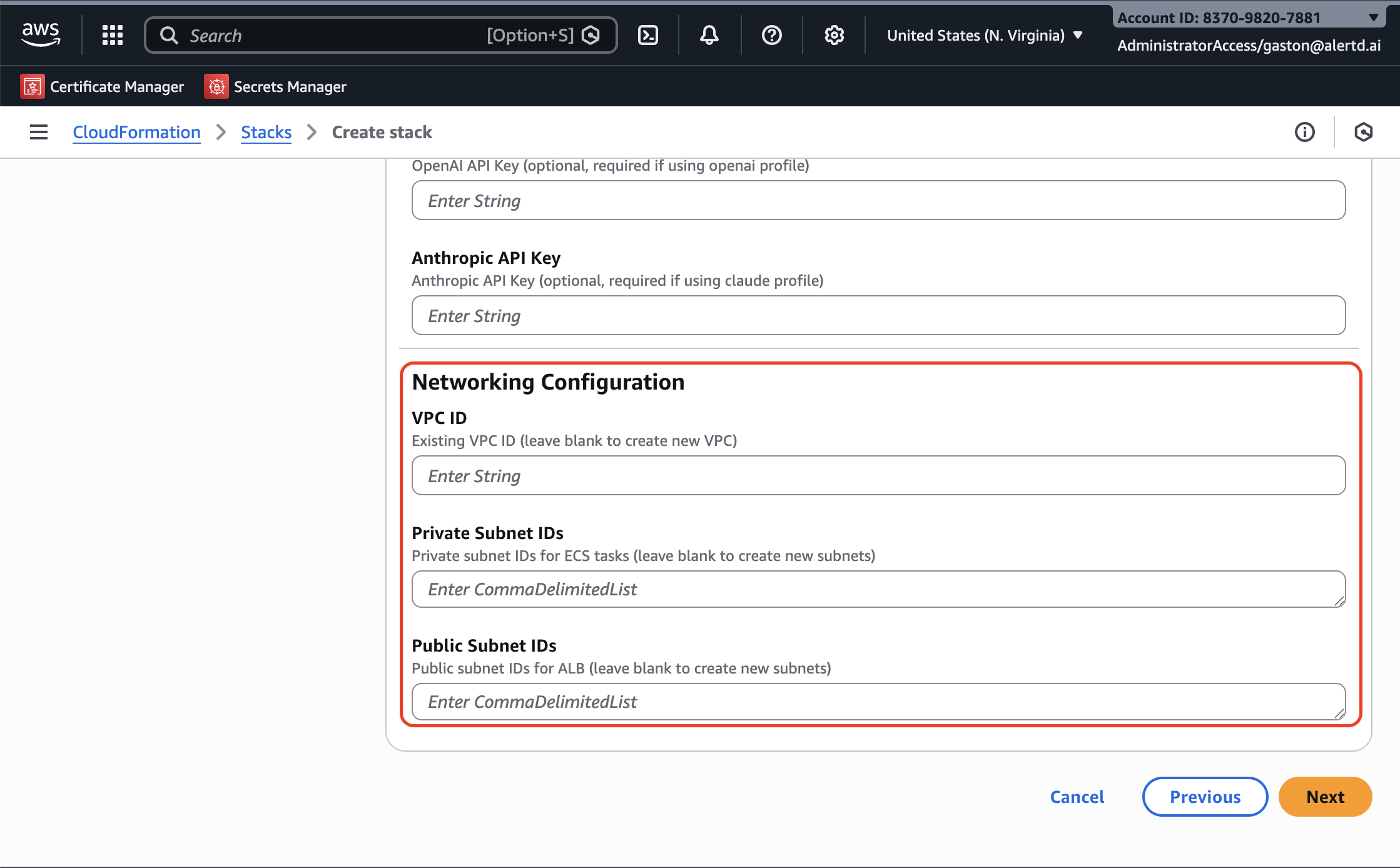
AlertD can deploy in a new VPC or use your existing network infrastructure.
Option A: New VPC (Default)
Leave all fields blank, and CloudFormation will automatically create:
- New VPC with public and private subnets across 2 availability zones
- NAT Gateway for private subnet internet access
- Security groups and routing tables
Option B: Existing VPC
If deploying into an existing VPC, provide:
- VPC ID: Your existing VPC identifier (e.g.,
vpc-0123456789abcdef0) - Private Subnet IDs: Comma-separated list of private subnet IDs for ECS tasks
- Example:
subnet-abc123,subnet-def456 - Must have outbound internet access via NAT Gateway
- Example:
- Public Subnet IDs: Comma-separated list of public subnet IDs for the load balancer
- Example:
subnet-ghi789,subnet-jkl012
- Example:
When using existing VPC, ensure subnets span at least 2 availability zones for high availability.
Click Next to continue.
Step 7: Configure Stack Options
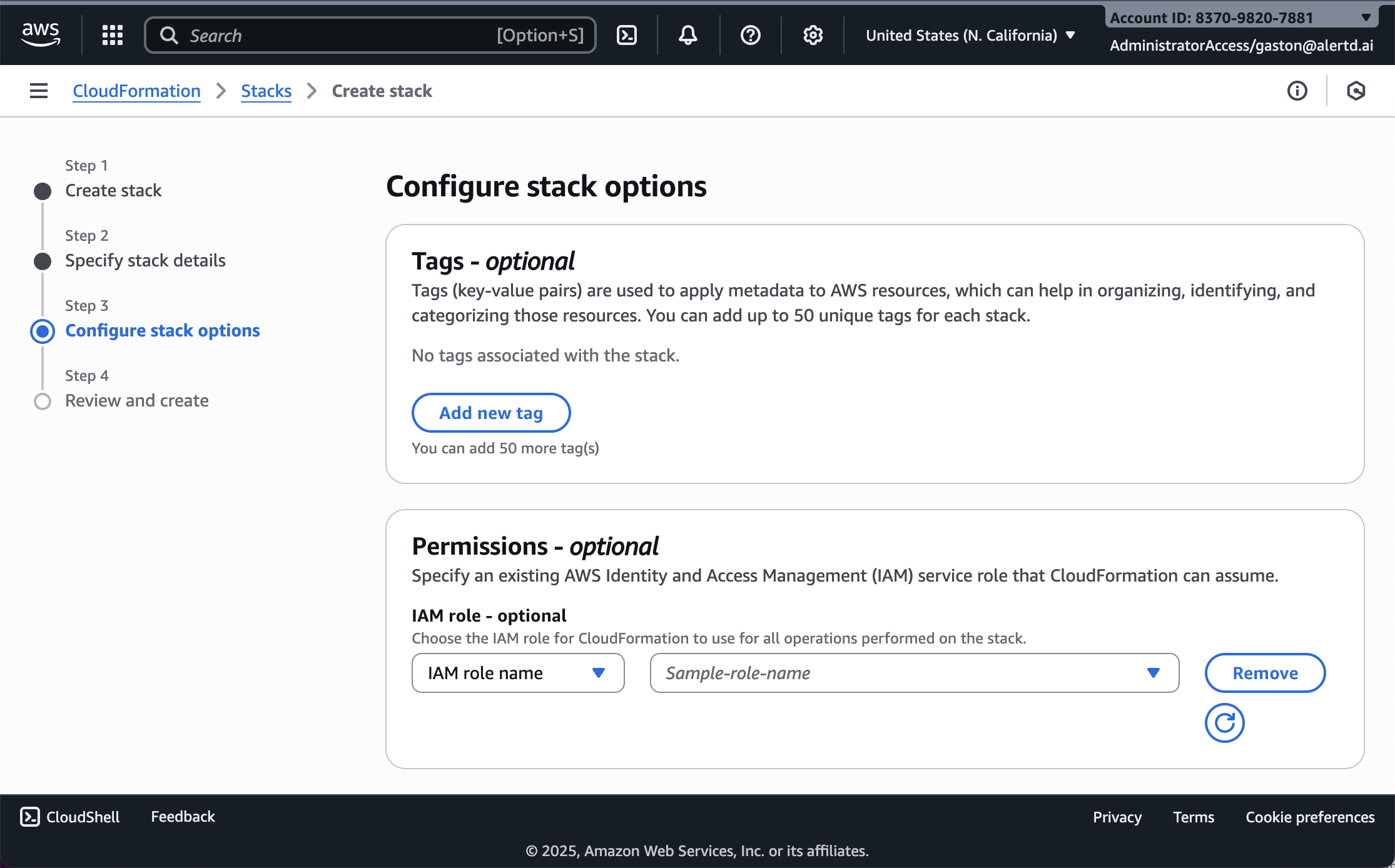
On the Configure stack options page:
- (Optional) Add tags to help identify your resources
- Example:
Environment: Production,Team: DevOps
- Example:
- (Optional) Assign an IAM Role for CloudFormation
- Leave blank to use your current credentials
- Keep rollback, notification, and timeout settings as default
Scroll down to the capabilities section.
Step 8: Acknowledge IAM Resource Creation
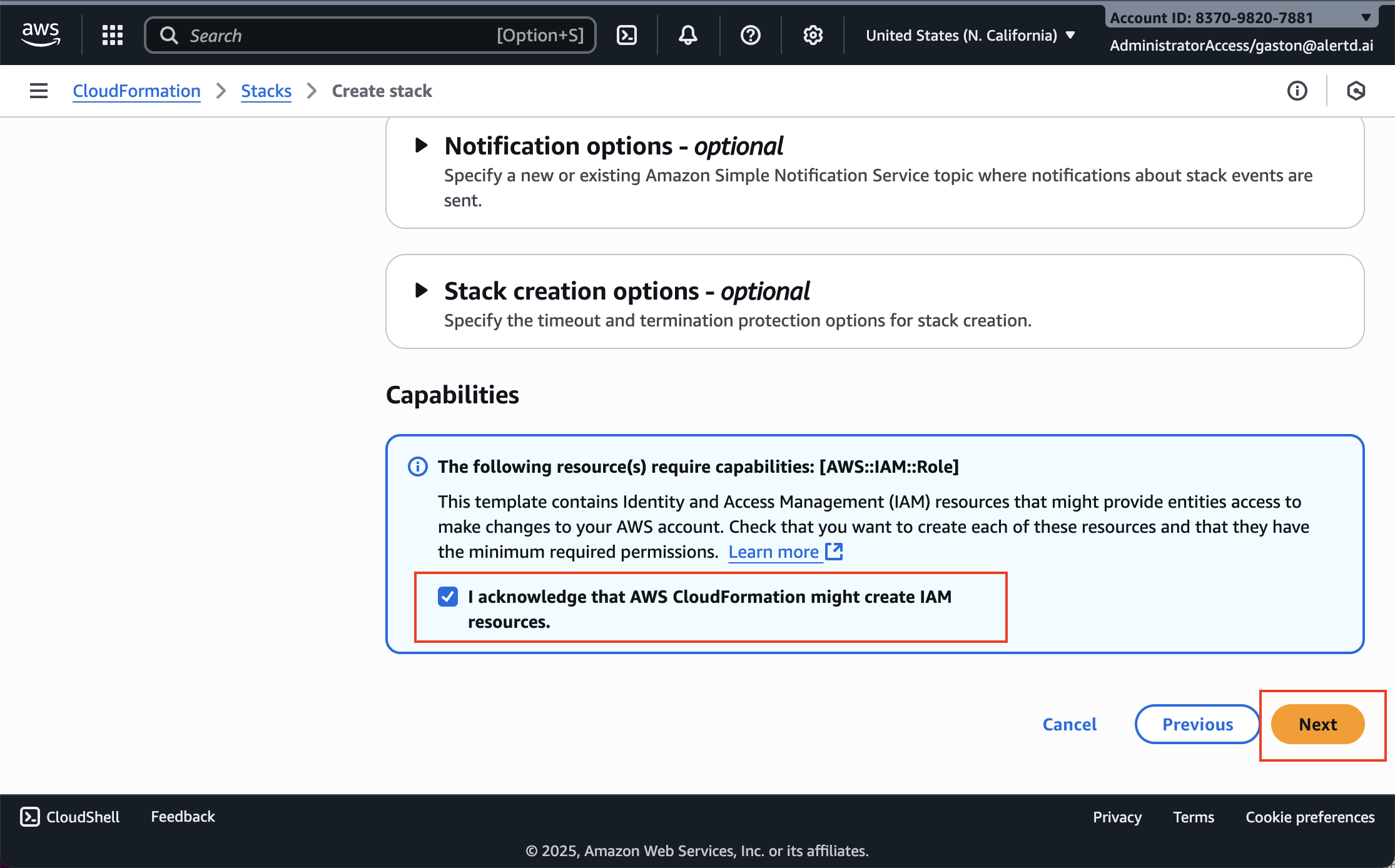
CloudFormation needs permission to create IAM roles and resources for AlertD.
- Locate the Capabilities section at the bottom of the page
- Check the box that states:
☑ I acknowledge that AWS CloudFormation might create IAM resources.- This acknowledgment is required because AlertD creates:
- ECS task execution roles
- Service-linked roles for ECS and ELB
- CloudWatch logging roles
Click Next to proceed to the review page.
Step 9: Review and Submit
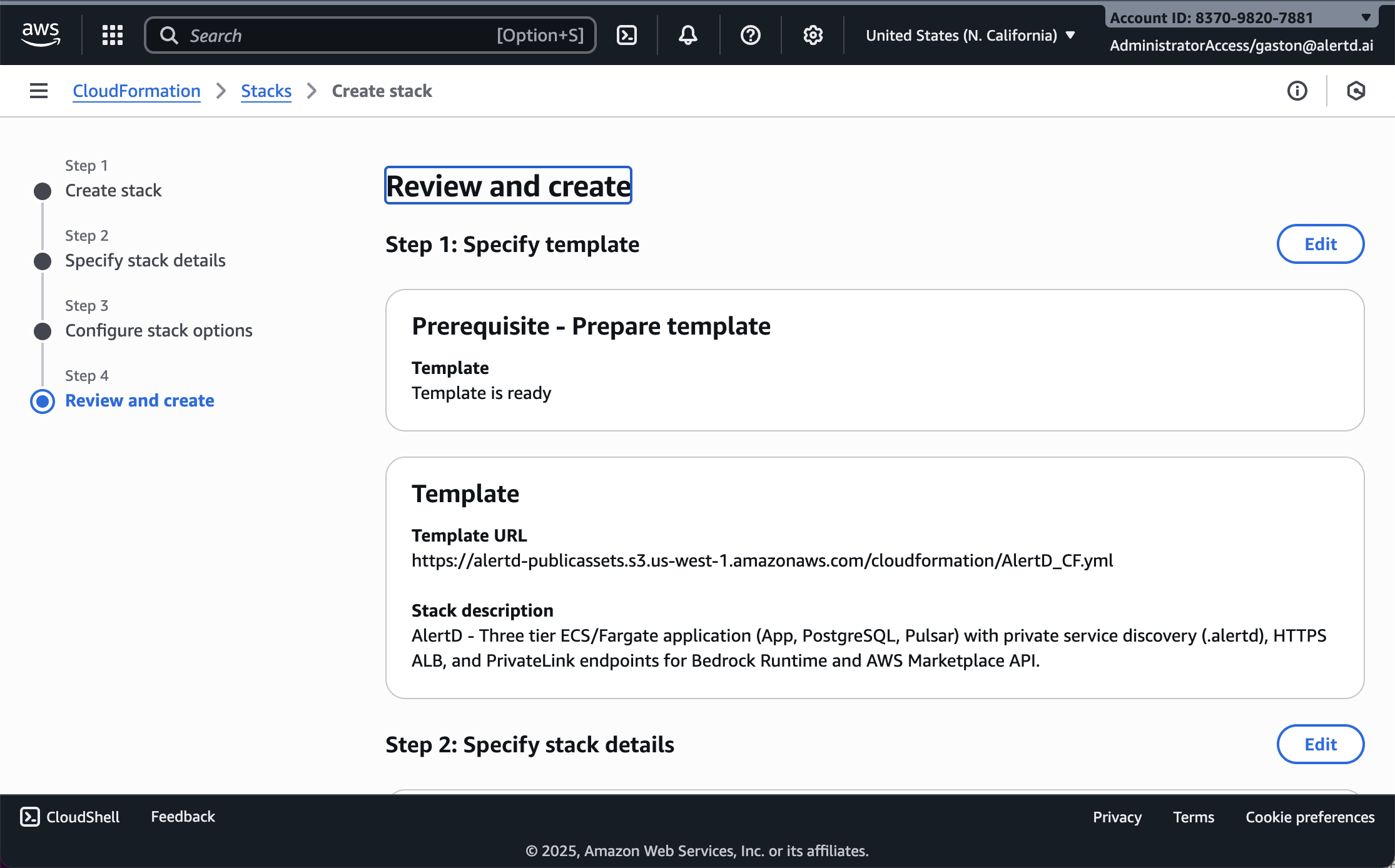
The Review and create page displays a summary of all your configuration:
Review These Critical Settings:
- Template URL: Verify it points to the AlertD CloudFormation template
- Stack Name: Confirm stack name is correct
- Certificate ARN: Double-check your ACM certificate ARN
- Model Configuration: Verify your chosen LLM provider and API key (if applicable)
- Networking Configuration: Confirm VPC and subnet settings
Submit the Stack
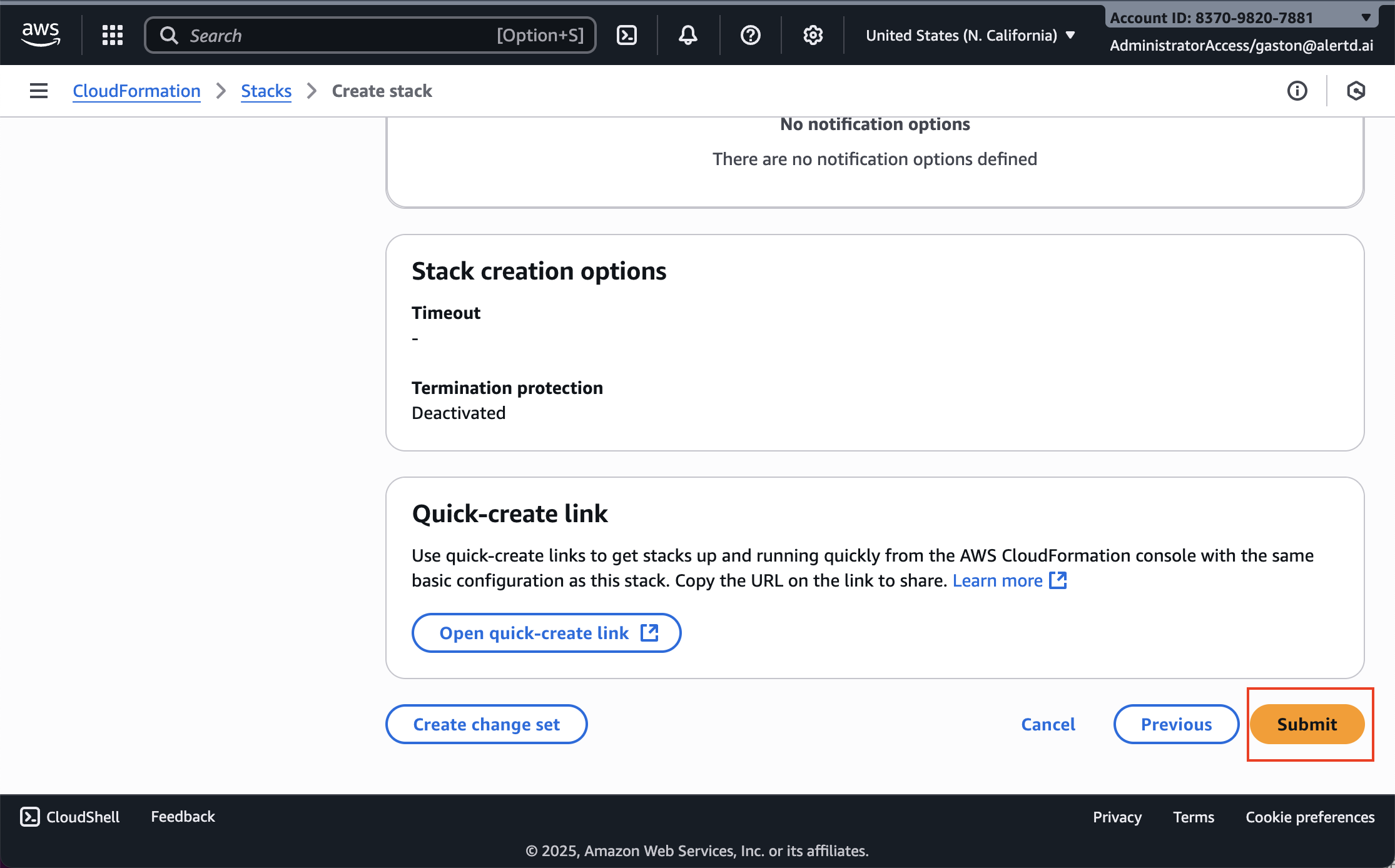
- Carefully review all parameters
- If everything looks correct, click Submit at the bottom of the page
- CloudFormation will begin creating your AlertD infrastructure
Step 10: Monitor Stack Creation
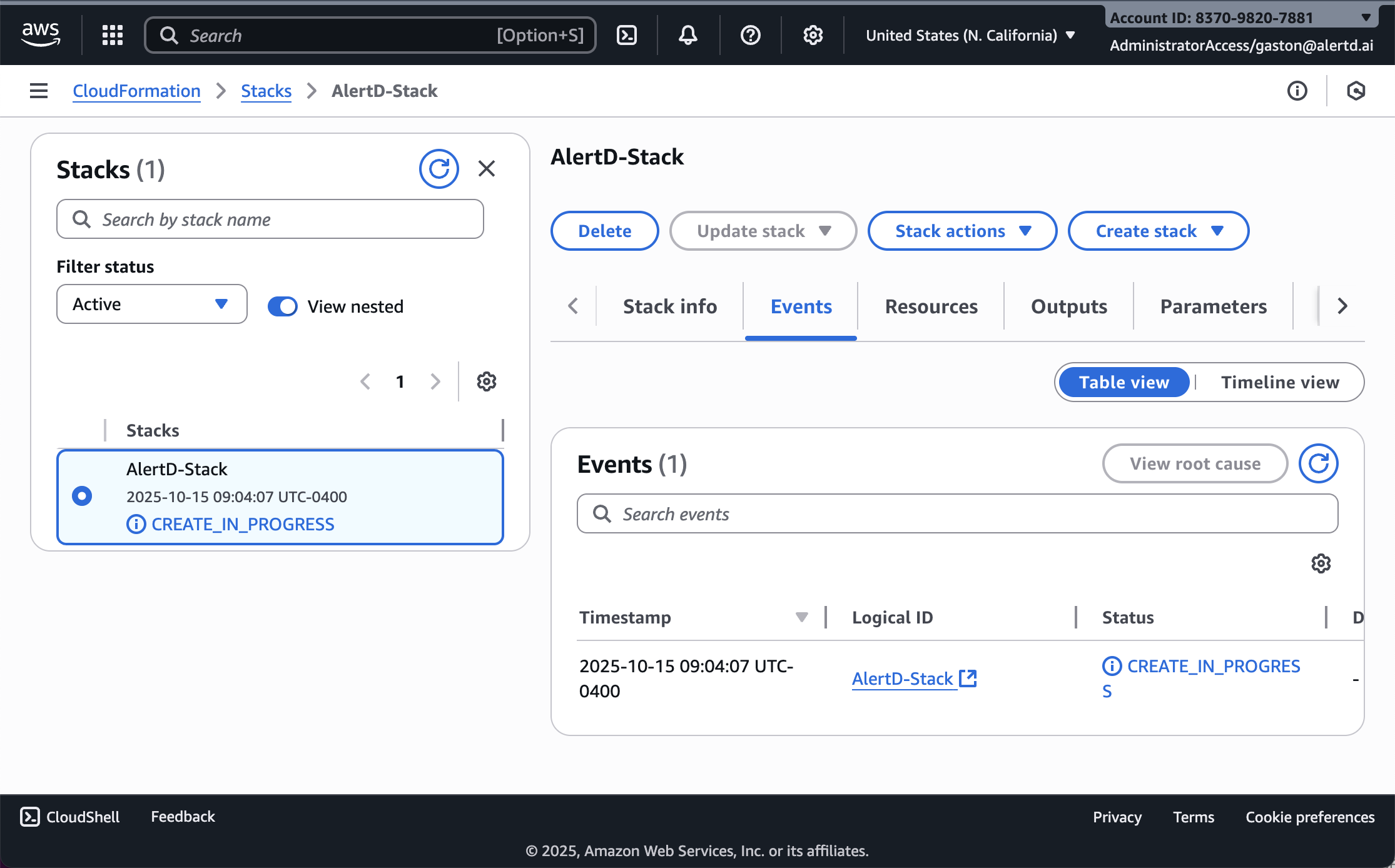
After submission, CloudFormation begins provisioning resources:
- The stack status will show CREATE_IN_PROGRESS
- You can monitor progress in the Events tab
- CloudFormation creates resources in this order:
- VPC, subnets, and networking components (if new VPC)
- Security groups
- ECS cluster
- PostgreSQL and Pulsar task definitions
- Application task definition
- Load balancer and target groups
- ECS services
Expected duration: 10-15 minutes
You can safely close this window and return later. CloudFormation will continue running in the background.
Step 11: Verify Stack Completion
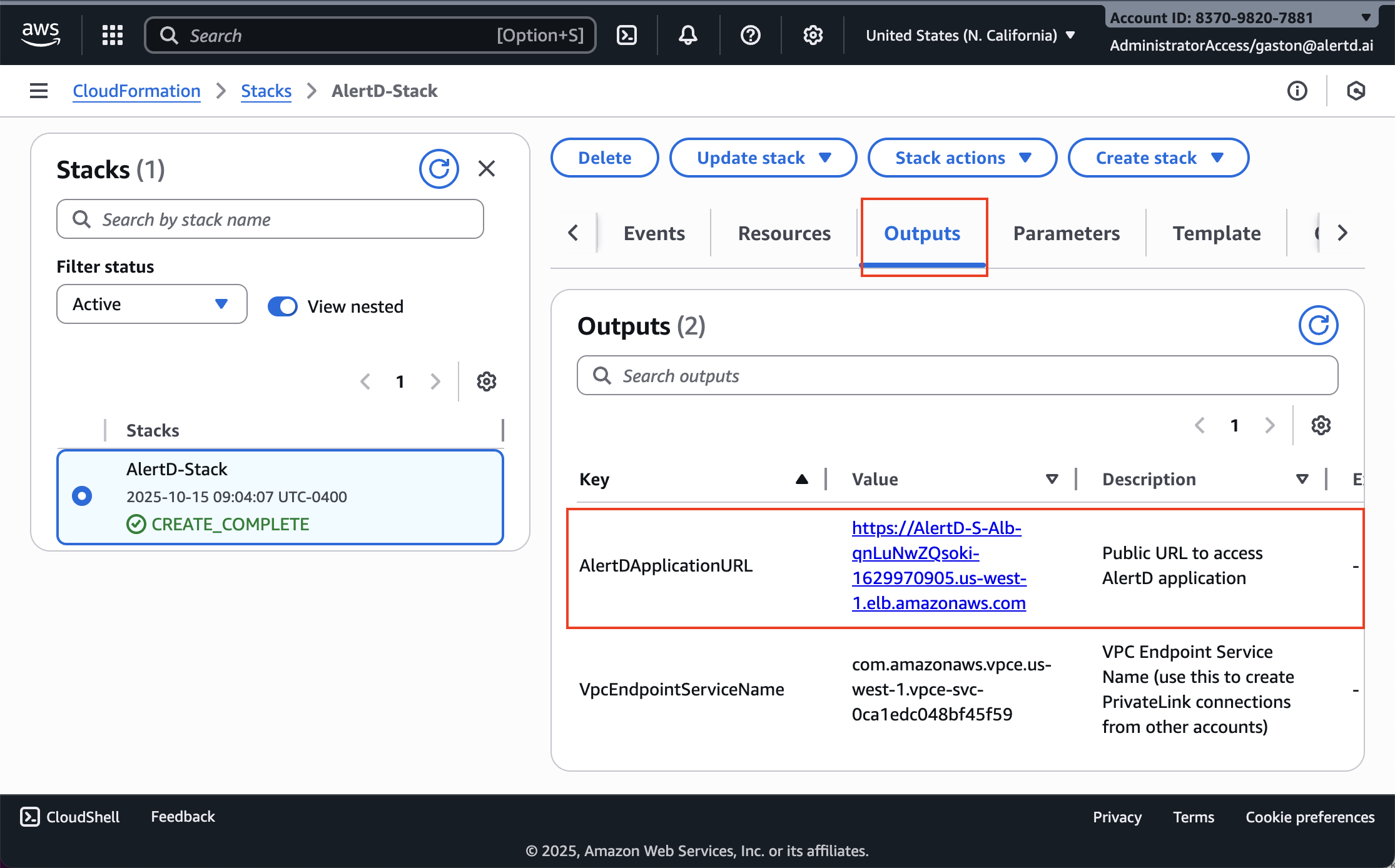
When deployment finishes:
- The stack status updates to CREATE_COMPLETE (green checkmark)
- Click the Outputs tab
- Record the following important values:
Critical Outputs
AlertDApplicationURL
- The public URL for accessing your AlertD web application
- Format:
https://AlertD-S-Alb-xxxx.us-west-1.elb.amazonaws.com - You’ll use this URL to access AlertD and complete setup
VpcEndpointServiceName
- Used for creating PrivateLink connections (if required for private deployments)
- Format:
com.amazonaws.vpce.us-west-1.vpce-svc-xxxx - Share this with AlertD support if needed for design partner access
Save these outputs! You’ll need the AlertDApplicationURL in the next step.
Step 12: Configure DNS (Recommended)
For production use, you should map your custom domain to the AlertD load balancer.
Create a DNS Record
In your DNS provider (e.g., Route53, Cloudflare), create a CNAME record:
Type: CNAME
Name: alertd.example.com
Value: <AlertDApplicationURL from CloudFormation Outputs>Example:
alertd.example.com → AlertD-S-Alb-abc123.us-west-1.elb.amazonaws.comVerify SSL Certificate
- Ensure your ACM certificate covers the custom domain you’re using
- The certificate should be validated before DNS propagation completes
- DNS changes typically propagate within 5-60 minutes
✅ Deployment Complete!
Your AlertD infrastructure is now running in your AWS environment. The application consists of:
- ECS Fargate Cluster running AlertD app, PostgreSQL, and Pulsar services
- Application Load Balancer routing HTTPS traffic to the application
- Private Service Discovery for internal service communication
- CloudWatch Logs capturing application logs
- Secrets Manager storing database credentials securely
Resources Created
The CloudFormation stack created approximately 30-40 resources including:
- VPC with public/private subnets (if new VPC option selected)
- NAT Gateway and Internet Gateway
- Security groups for each service
- ECS task definitions and services
- Application Load Balancer with listeners and target groups
- CloudWatch log groups
- Service discovery namespace
Next Steps
Now that AlertD is deployed, you need to complete the initial setup:
- Access the application using the AlertDApplicationURL
- Authenticate with Google or GitHub
- Create an IAM role for AWS resource access
- (Optional) Configure Slack integration
Troubleshooting
Stack Creation Failed
If your stack fails to create:
- Check the Events tab for error messages
- Common issues:
- Invalid certificate ARN or certificate in wrong region
- Insufficient IAM permissions for the deploying user
- VPC subnet configuration errors (if using existing VPC)
- API key issues (if using OpenAI or Anthropic)
Rollback Occurred
If CloudFormation rolled back:
- Review the failure reason in the Events tab
- Delete the failed stack
- Fix the issue (certificate, permissions, etc.)
- Restart deployment from Step 1